
Check Point Capsule Cloud
A cloud based mobile security container to enforce your in-network
security policy on laptops used outside of the corporate
network

Your employees expect to do their work whenever and wherever it's convenient, but their use of laptops and online behaviors can put your corporate network at risk. Check Point Capsule Cloud solves this security dilemma by using a cloud based mobile security container to enforce your in-network security policy on laptops used outside of the corporate network.
Sorry, this product is no longer available, please contact us for a replacement.
Overview:
Historically, organizations enforced corporate security policies to protect all devices and data within the traditional corporate network from being exposed to threats. Over the last several years, the traditional network has disappeared. Organizations have evolved, and are confronting a situation where business data is accessed from everywhere, and travels outside the network. The increased need for business continuity and the associated risks posed by laptops create a huge challenge for security professionals.
As more and more workers access corporate and business data remotely, new gaps are opened within the organization's infrastructure. Laptops can expose users and organizations to new sources of attacks. Without knowing it, you may have accessed a malicious site, or downloaded a virus unintentionally.
Security "blind-spots" like these expand as employees use laptops to consume business data from anywhere and everywhere they go. Organizations need to provide the same level of protection for laptops and remote offices as they provide for the devices within the confines of the corporate network perimeter.
Solution
Check Point Capsule enables organizations to provide security continuity across their business operations, providing always-on, always up-to-date protection for users outside the organization's security perimeter.
With Check Point Capsule, organizations are able to leverage protections from all Check Point Software Blades as a cloud-based service, protecting the network and their users from threats everywhere they go; preventing suspicious file downloads, blocking malicious websites, and stopping bots before they have a chance to cause damage.
Check Point Capsule offers real-time protections by directing all traffic from laptops through a secure tunnel to the cloud where corporate policies are enforced. A single policy can be applied for both on premise and off premise laptops that is centrally managed through SmartDashboard or remotely through an intuitive web user interface for pure cloud deployments.
With 24/7/365 coverage by Check Point experts, and datacenters located around the globe, organizations can truly provide always on and always up-to-date protection for their entire network and users. Whether on premise or outside the enterprise security perimeter, organizations can ensure their assets, data, and devices are protected.
Key Features
- Includes IPS, Application Control, URL Filtering, Antivirus, Anti-Bot, and Threat Emulation
- Data centers located across the globe
- Supported on Windows & Mac platforms
- Single Sign-On (SSO)
- Logs can be pushed and stored locally or viewed online
- Active Directory integration for identity awareness
Key Benefits
- Extend corporate security policy to Windows and Mac laptops
- Prevent download of suspicious files, access to malicious websites, and bot damages on laptops.
- Protect users outside the enterprise security perimeter
- Extend Check Point security to remote offices without security appliances
- Real-time protection against web threats
- Apply a single security policy for both on and off premise laptops
- Deliver the protection of Check Point Software Blades via a cloud-based service
- Always up to date and fully tuned software
Features:
Extend corporate security policies to Windows and Mac laptops
Check Point Capsule enables organizations to extend the same policies from their corporate network to protect laptops and remote offices, wherever they are. With Check Point Security Management, organizations can manage policies in the cloud the same way they manage any other gateway, by simply adding a network object for the cloud to the relevant policy rule. Once the policy is implemented, it will automatically propagate to all on premise gateways and extend the corporate security policy to the cloud.
Protect users outside the enterprise security perimeter
Check Point Capsule facilitates the use of Windows and Mac laptops on the go. All traffic is directed to the cloud service using a secure tunnel. No user data is sent in the clear. Each packet gets scanned for both inbound and outbound traffic to ensure it is safe for use.
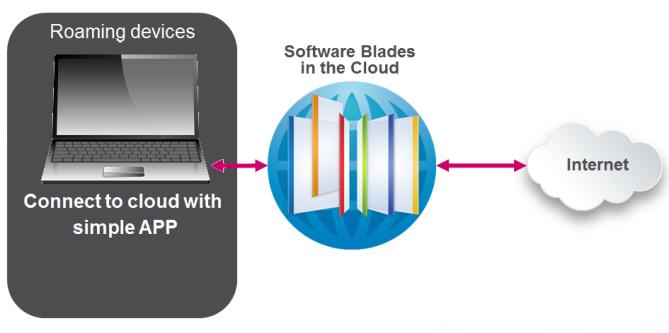
Prevent access to malicious files, websites, and bot damages
With Check Point Capsule, organizations are able to leverage protections from all Check Point Software Blades as a cloud-based service, protecting the users and their network from threats everywhere they are. In addition to laptop users, remote offices can leverage the security service by connecting their local appliance to the cloud, extending corporate security without the need to deploy additional hardware.
Powered by Check Point ThreatCloud, up-to-date protections provided by IPS, Application Control, URL Filtering, Antivirus, Anti-Bot, and Threat Emulation ensure that users and remote offices are protected from downloading malicious files, accessing risky websites, and stop bot communications before damage is caused.
Maintain full visibility with a single, integrated management platform
Check Point Capsule can be managed through Check Point Security Management, allowing for seamless integration into existing Check Point deployments. Logs are sent from the cloud directly to Check Point Security Management, giving organizations centralized visibility of log activity.
Policies can also be managed from the intuitive web user interface. Available from any browser, the easy to use web user interface requires no extra license or installation. All logs are consolidated by the service and available from the web user interface, enabling full visibility and management of Check Point Capsule.
Seamless client installation and distribution
Check Point Capsule is easy to implement. Client installation supports Group Policy Object (GPO) distribution and Single Sign-On (SSO). Once installed, the client configures itself. There is no need for an administrator to configure it. Check Point Capsule integrates with active directory for identity awareness. In addition, the client is network aware, and able to disconnect itself when working within the corporate LAN.
Powered by Check Point ThreatCloud
Newly discovered threats are sent to ThreatCloud, which can then protect other Check Point connected gateways. Each newly discovered threat signature is distributed to other Check Point connected gateways and the cloud to block the threat before it has a chance to spread. This constant collaboration makes the ThreatCloud ecosystem the most advanced and up-to-date threat network available.
Technical Specifications:
| Provided Technologies |
|---|
|
| Client Platform Support |
|
Documentation:
Download the Check Point Capsule Cloud Datasheet (PDF).
Pricing Notes:
- All Prices are Inclusive of GST
- Pricing and product availability subject to change without notice.
- Check Point Capsule licensed per user and defined as annual service.
- The per user license covers up to 3 devices per user.
- 3 packages exist: Capsule Total, Capsule Cloud, Capsule Workspace and Docs.
- The Capsule Total package includes the Cloud, Workspace and Docs.

