
Check Point Security Checkup
Discover Security Vulnerabilities and learn how to fix them!

Contact us to sign up for your Security Checkup
Overview:
Your corporate network offers access to valuable and sensitive information. Information that must never fall into the wrong hands.
Can you be sure there aren’t any hidden “surprises” threatening your most precious data assets? No stealthy malware, back doors, data leaks or other security vulnerabilities?
In order to understand what are the critical security threats organizations are exposed to today and should be addressed in 2014 and beyond, the Check Point security research team analyzed event data from more than 10,000 organizations world wide in 2013. The Check Point 2014 Security Report presents the results of our research.
The highlights of our research:
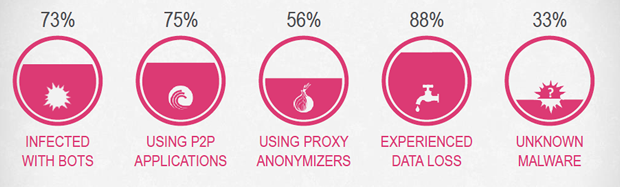
- 73% of organizations were found infected with bots.
- In 75% of organizations P2P file sharing applications were detected in use by employees. P2P applications open a backdoor into the corporate network might cause data leakage and malware infections.
- In 56% of organizations Proxy Anonymizer applications were detected in use by employees. Anonymizers applications bypass security and hide user’s web activity.
- 88% of organizations experienced at least one potential data loss incident.
- Our research found that 33% of organizations downloaded at least one unknown form of malware. The malware was embedded mainly into PDF, EXEs, archives or Microsoft Office files. Unknown malware refers to zero-days or new forms of malicious code that exploit software vulnerabilities and cannot be detected at the time of exploitation, even by up-to-date antivirus, anti-bot or Intrusion Prevention System (IPS) solutions.
According to these statistics, most organizations are vulnerable to security threats.
Which security threats are your organization exposed to? Early exposure of hidden threats will enable you to and address these risks on time and enhance the security your organization.
Check Point introduces it’s Security Checkup assessment. In a similar way that a doctor gives you a medical health check to help you understand your health status, a Security Checkup provides a security status of your organization’s networks. It will uncover security threats your organization is exposed to.
At the end of this assessment, you will get a threat analysis report that includes all the security incidents detected during the assessment and a set of recommendations on how to protect against these threats. A security expert will discuss the findings with you and how they can be prevented.
More than 4,000 Security Checkup assessments have been conducted so far world wide helping organizations of any size and industry be more secure. We offer you the opportunity to conduct a Security Checkup in your organization as well.
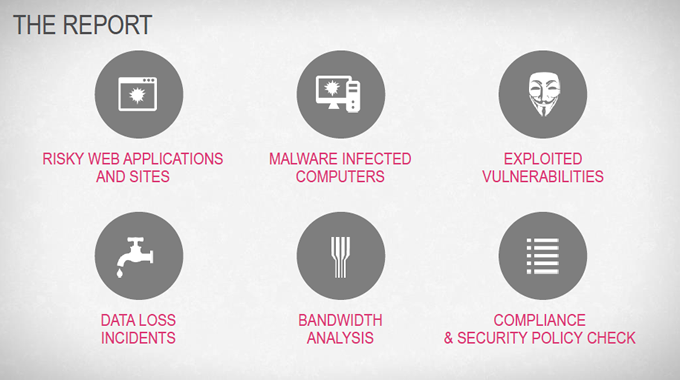
Check Point offers an onsite security assessment that will provide you with a comprehensive threat analysis report identifying:
- Access to high risk web applications
- Malware infected computers
- Exploited vulnerabilities and attacks on your network
- Data leakage incidents
- Recommendations to protect your network from
Key Benefits:
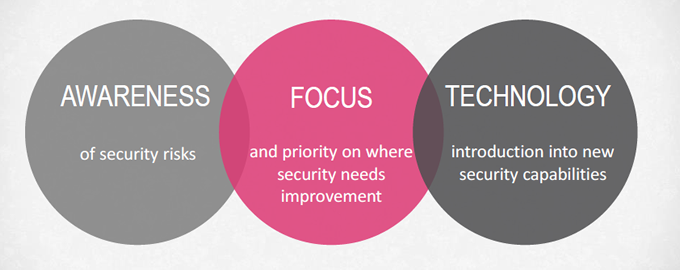
- Better awareness of the security risks you are exposed to and may not have been aware of.
- The Security Checkup also helps to point out and prioritize the security gaps that require improvement.
- And finally, you are being introduced to the latest security technology that covers all aspects of network security. This is the part where our expert will help you to address any security issues and can make your organization more secure. Our security experts can be your advisor.
What's Included in the Security Checkup:
The report covers a full range of security risks:
- High risk web applications and websites used by employees such as: P2P File Sharing applications, Proxy anonymizers, File Storage applications, malicious websites and more.
- Analysis of malware threats which include computers infected with bots, viruses and also unknown malware (zero days and malwares that cannot be detected by traditional anti-virus systems.
- Exploited vulnerabilities of servers and computers in the organization indicating possible attacks.
- Sensitive data sent from inside the organization outside the organization via emails or web.
- Bandwidth analysis listing the top bandwidth consuming applications and accessed websites that can help organizations understand who and what is hogging your network bandwidth.
- Compliance and best practices, this section is only relevant to existing Check Point customers with an active Security Management. This section compares the current rule base configuration with Check Point best practices recommendations and also provides a compliance check of the rule base with many of the known industry standards (such as PCI, HIPAA, ISO etc…).
The report also helps to understand what is needed in order to protect against the detected risks. The report includes a section with recommendations on how to protect the organization from these threats.
How does this work?
The assessment is conducted on-site by security experts and includes four main steps:
- The first step sees the security expert set up a Check Point Security Gateway on which the assessment will be conduced. All relevant Check Point Software blades are being activated and configured (For example: Application Control, URL Filtering, IPS, Anti-Bot, Anti-Virus, Threat Emulation, DLP, Identity Awareness if required, SmartEvent etc…)
- Next, the device arrives on-site and is plugged into the organization's network to inspect network traffic, without any network downtime and without any need for changes in network configuration. We will discuss how this is being done on the following slides. It is recommended to leave the unit to inspect traffic for at least a week so enough traffic is monitored (but a few days can be enough in some instances). The longer the time period, the better. The assessment can be conducted to either existing Check Point customers or net new customers.
- In the next step, the security expert will remove the device from the network, analyze the results, and generate the Security Checkup report.
- In the final step the security expert will present the findings and have an open discussion about security technologies and about security solutions to protect your network and address the weak points detected in the report.
The report is designed to bring value to anyone in the organization that has a concern with the current security status. It is designed to be easy to read on all levels, even by non security experts.
It makes C-level executives aware of the security status within their organization and helps them find out if there are any critical risks that require immediate attention.
The report also helps security officers validate the organizational security policy and check whether there are any gaps which require urgent actions, enabling enhancement of their current security architecture.
In addition, security administrators can check their current security configuration. Security incidents might indicate that there are some misconfigurations, over permissive security configurations or even limitations in current security solutions.
And finally, the report provides operators of the Security Operation Center (SOC) an additional source of visibility into the organizational security posture. Uncovering new security risks they were not aware of such as malware infected computers, might indicate that the existing SOC systems does not provide the security coverage they need.
Connecting a Security Checkup device into a network might raise the concern of network downtime. We are aware of organizations policies for zero network downtime. We also know that IT network teams are usually reluctant about plugging an external device into their network and/or changing their current network configuration.
To avoid any risk of downtime and eliminate the need to change network configuration, the Security Checkups have the option of using a Monitor Port (configured on the Security Checkup device). To inspect traffic, the Monitor Port connects to a Mirror Port (also known as Span Port) on a network switch or to a TAP device (Test Access Point). It means that only copied network traffic is being inspected and by that it removes all the challenges of inline connectivity. The Monitor Port does not transmit any traffic to the network and in this way there is no downtime risk and no change to the existing network configuration.
Privacy:
The Security Checkup assessments exposes security incidents and risks which is usually sensitive information for organizations. What about the privacy of this information and what if your policy does not allow us to plug 3rd party devices into your network?
We fully respect our customer's privacy. After all, we are a security company.
After monitoring traffic, usually the analysis of the findings and the report creation are done off premise to save customer's time while analyzing the results, however the report can also be generated on-site and the logs can be deleted before the security expert leaves the premises.
To make is even more private, the whole assessment can been done on-site, end to end including the setup stage. If the organizational policy does not permit a 3rd party device plugged into the network, there is also an option to install the Security Checkup device on-site by using a server which will be provided by you (the Hardware needs to be supported by Check Point’s Hardware Compatibility List, list available at http://www.checkpoint.com/services/techsupport/hcl/). This way nothing is being brought from outside the organization and nothing is leaving the premises.
Only under customer's agreement we collect anonymized information for statistical purposes. This data does not include any information that can reveal the organization identity.
Video:
Documentation:
Download the Check Point Security Checkup Sample Report (PDF).

