Check Point IoT Security for Networks and Devices (Quantum IoT
Protect)
Scalable Performance, Advanced Security


Checkpoint Quantum IoT Protect
Contact us
for Pricing!
Get a Quote
- Web Application Protection
- API Security
- Bot Prevention
- Intrusion Prevention (IPS)
Overview
Protecting IoT Devices
With 63% of enterprises, 92% of industrial organizations and 82% of health care organizations using IoT, almost every company is exposed to cyber-attacks. IoT devices make life easier for businesses. Unfortunately, connecting IoT devices to the network extends the attack surface which provides more entry points for hackers.
- Identifying IoT security risks across IT/OT networks
- Creating policies to quickly secure IoT devices
- Preventing both network-based and device-level attacks
Key Benefits

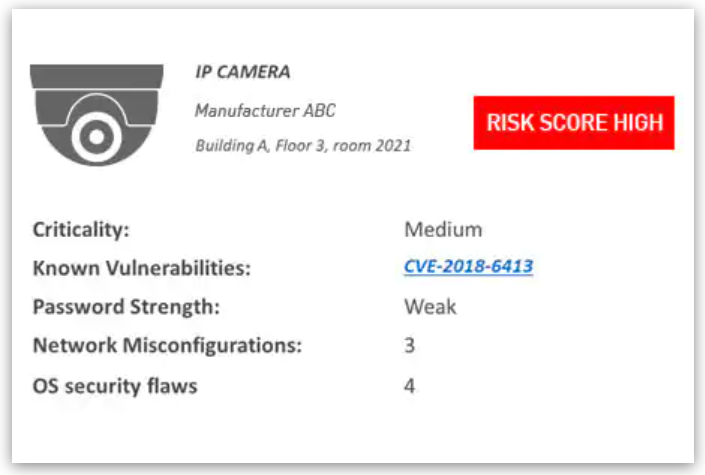
IoT Discovery & Risk Analysis
Uncover all the unmanaged and IoT devices in your network and their risks

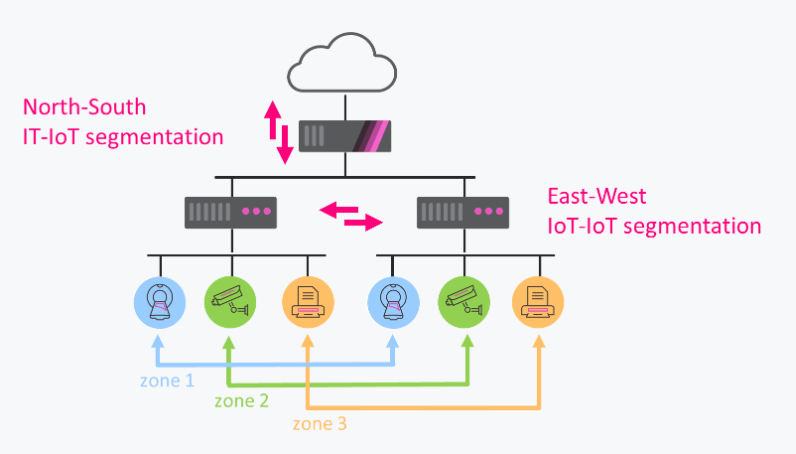
Zero-Trust Segmentation
Enforce zero trust policies to prevent unauthorised access and lateral movement

IoT Threat Prevention
Block known and zero-day attacks with virtual patching and real time IoT threat intelligence
Check Point IoT
Check Point IoT Protect prevents IoT cyber attacks, adapting protections to any IoT or OT device across smart-office, smart-building, medical and industrial environments.
Delivering zero-trust policy tailored per device, Check Point IoT Protect uses:
- Real time threat intelligence
- 60 innovative security services
- On-device runtime protection to deliver a complete, end-to-end prevention-first strategy for an ever-evolving cyberphysical world
Quantum IoT Protect

Enterprise
Secure smart building and smart office devices to prevent corporate spying and disruption to business operations.
While connecting Internet-of-Things (IoT) devices to your corporate network delivers clear benefits, it also exposes you to new cyber threats.
From IP cameras, and smart elevators, to routers and HVAC systems, IoT devices are inherently vulnerable and easy to hack. Furthermore, many of them are shadow unmanaged devices (connected to your network without anyone's knowledge).

Healthcare
Secure any connected device to ensure patient safety and ongoing healthcare services
Connecting IoT and medical devices to the clinical network improves hospitals' efficiency and quality of service. However, it also exposes them to new cyber threats.
From infusion pumps, patient monitors, and MRI machines to clinical refrigerators and even wheelchairs, many connected devices run on unpatched software, are misconfigured or use unsecured communication protocols. These flaws increase the risk of a successful cyber attack, where critical devices can be shut down, damaged, manipulated, or used to infect other systems on the network. These cyber attacks are mainly to steal patient data (PHI), or to launch ransomware attacks.

Industrial
Secure Operational Technology (OT) to ensure the safety and integrity of industrial operations
The increasing connectivity of industrial control systems (ICS) to the internet and the convergence of OT and IT networks introduces a growing attack surface to industrial manufacturing and critical infrastructure facilities.
Attackers can alter commands sent to controllers, to change the controllers' logical sequence or to change sensors' readings, thereby disrupting the industrial processes. These disruptions can manifest subtly so while they may be difficult to detect initially, they will cause increasing damage to processes over time.

Manufacturing
Get a powerful last line of defense for connected devices with on-device firmware-security
Embedded device manufacturers seek to offer customers devices that are secured against cyber threats arising from 3rd party supply-chain components, outdated firmware, newly discovered firmware CVEs and state-sponsored backdoors. To gain and instill confidence in customers, manufacturers need firmware-specific risk visibility and on-device runtime protection that blocks firmware attacks as they happen in real time.