
Check Point Infinity SOC
Achieving SOC Certainty

Check Point Infinity SOC
Contact us for Pricing!
Get a Quote
Expose, investigate and shut down attacks faster, with 99.9% precision across network, cloud, endpoint, mobile and IoT. These same intelligence and investigation tools are used by Check Point Research and are now available for you.
Because SOC Teams Deserve Certainty
For many SOC teams, finding malicious activity inside the network is like finding a needle in a haystack. They are often forced to piece together information from multiple monitoring solutions and navigate through a daily overload of alerts with little or no context. The result: critical attacks are missed until it’s too late.
Infinity SOC provides your team with the certainty it needs to expose and shut down attacks faster, before damage spreads. Easily deployed as a unified cloud-based platform, it increases security operations efficiency and ROI.
![]()
99.9% Precision
Expose and shutdown only real attacks
![]()
Rapid Investigation
With the industry's most powerful threat intelligence
![]()
Zero Friction
No deployment, integration and privacy pains
Watch the Product Tour
Watch the on-demand video to get a first-hand experience of all the features and capabilities of Infinity SOC.
Expose and Shut Down only REAL ATTACKS
Across Network, Cloud, Endpoint, Mobile and IoT
Infinity SOC uses the power of AI to accurately pinpoint real attacks from millions of daily logs and alerts. It enables you to quickly respond to the most severe threats with automated triage and a single-click remediation.
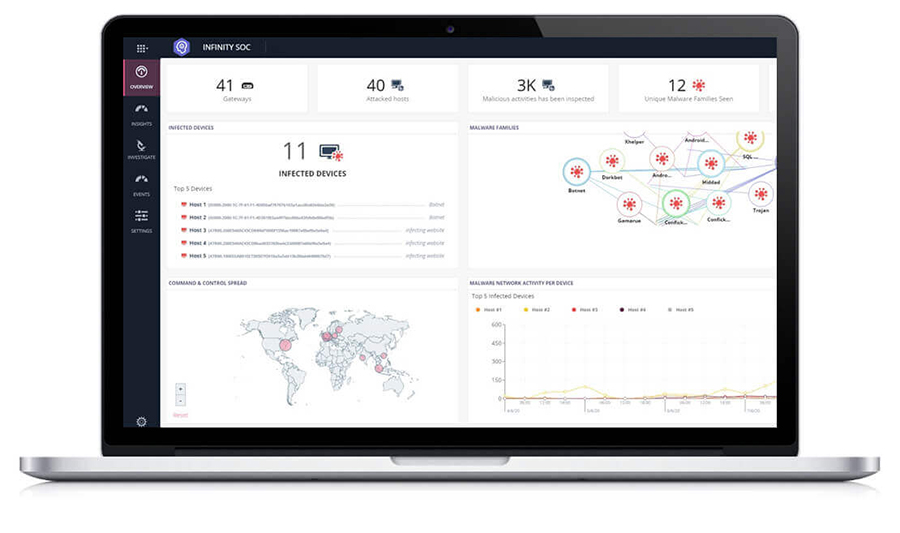
From Millions of Logs to Only Real Alerts
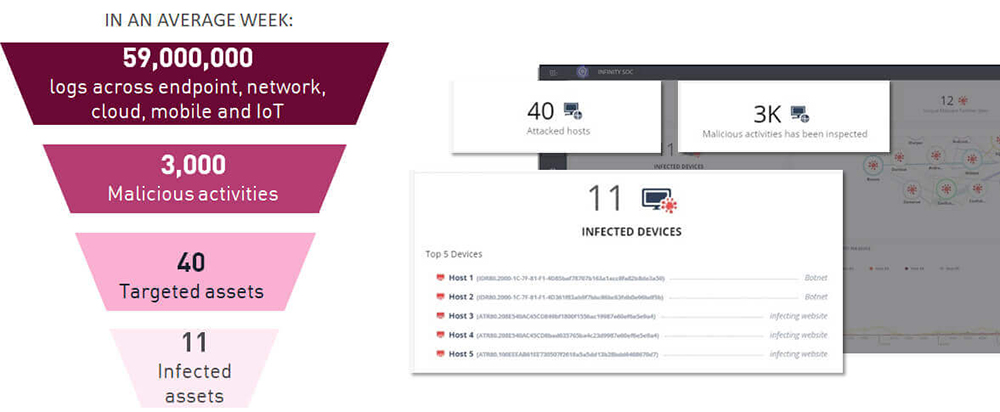
Automated Triage
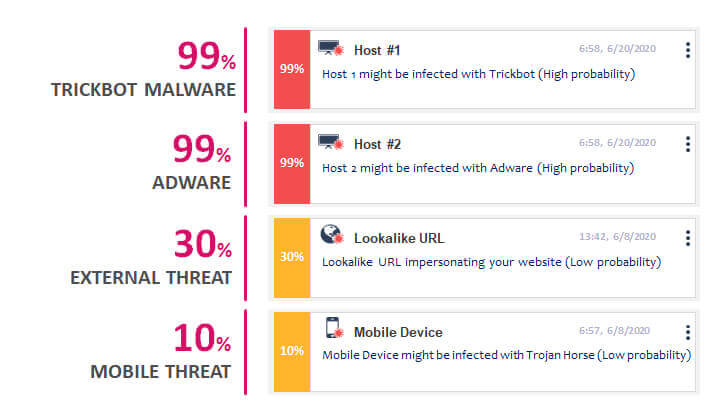
Respond Intelligently Based On Severity and Probability
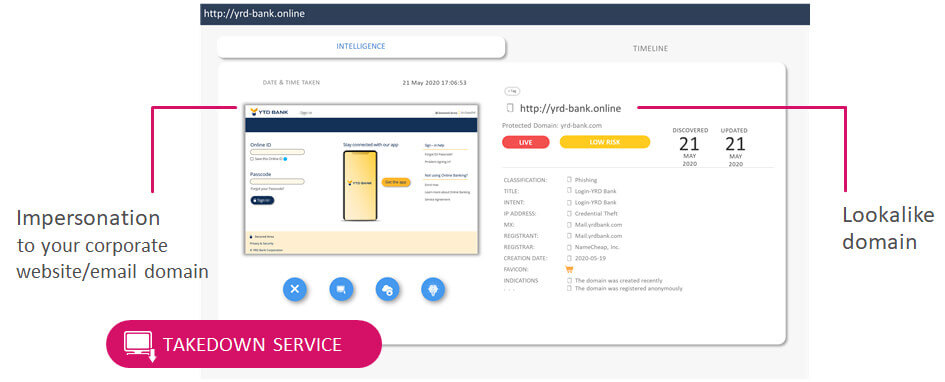
External Threat Visibility
Prevent Phishing Campaigns Against your Customers and Employees
Minimize the Attack Impact With a Single-Click Remediation
-
1 Install lightweight client on infected host
- Identify and kill all malicious processes
- Block C&C communications
- Delete all installed malicious files
- 2 Get a detailed forensics report with actionable insights
With Check Point Smart-1 Cloud, Your Management is Auto Scaled
On Demand
No Physical Limits!
Add as many gateways as you please!
Keep logs indefinitely.
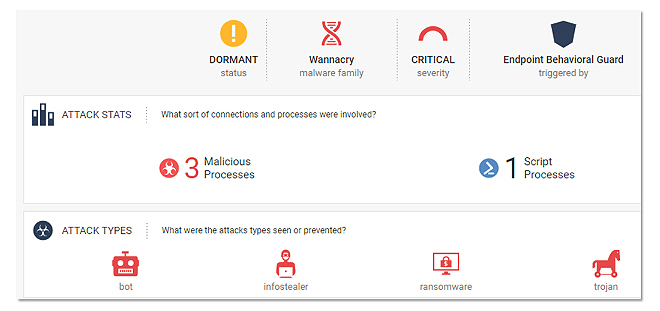
Uncover Even the Stealthiest Attacks with 99.9% Precision
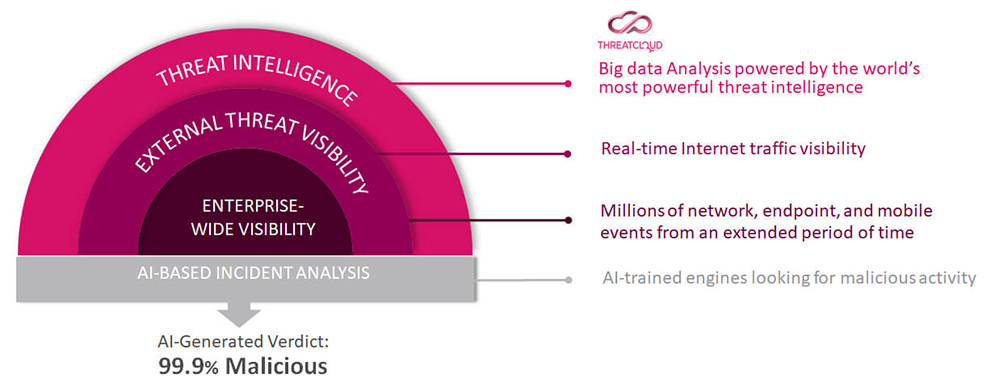
Accelerate and Deepen Investigations With the World's Most Powerful Threat Intelligence
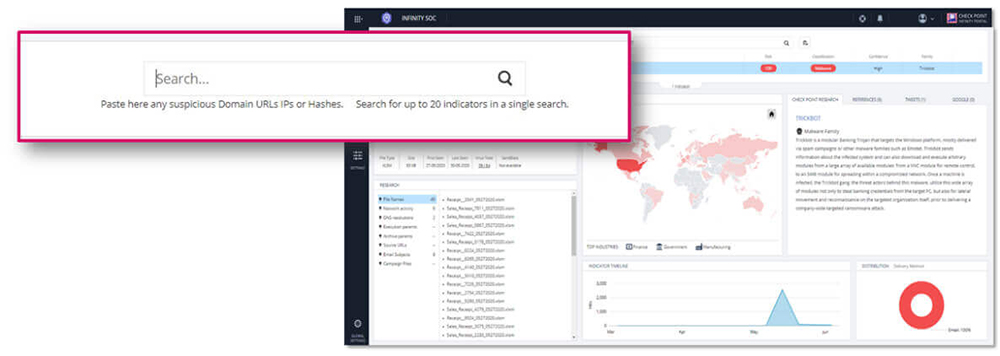
‘Google search’ any IoC from a centralized portal and quickly get highly processed threat intelligence and unique research data.
Use exclusive investigation tools developed by the Check Point Research Team and used daily to expose and investigate the world’s most dangerous and sophisticated cyber-attacks.
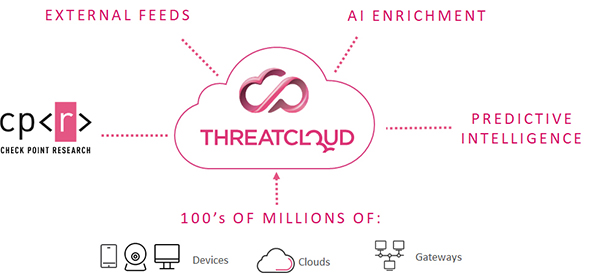
Fueled by the Power of ThreatCloud
Real-time threat intelligence derived from hundreds of millions of sensors worldwide, enriched with AI-based engines and exclusive research data from the Check Point Research Team.
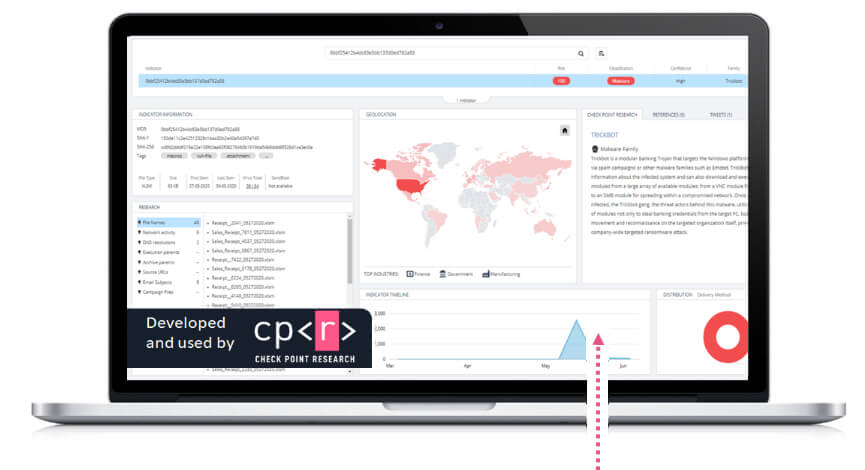
'Google Search' Any IOC from a Centralized Portal
Get highly processed intelligence and exclusive research data on geographical spread, targeted industries, attack timeline and patterns, malware DNA, and more.
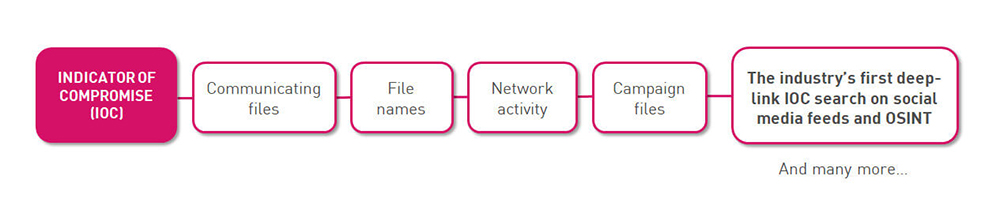
Obtain Exclusive Intelligence to Deepen Investigations
Quickly Determine Whether a Suspicious File is Malicious
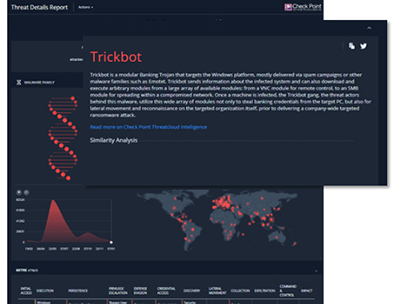
Use SandBlast's threat emulation service, which has the industry's best catch rate.
Threat Emulation report insights include:
- Malware family
- Geos targeted
- MITRE ATT&CK techniques
- Emulation videos
- Dropped files
- C2 URLs
- And More!

