
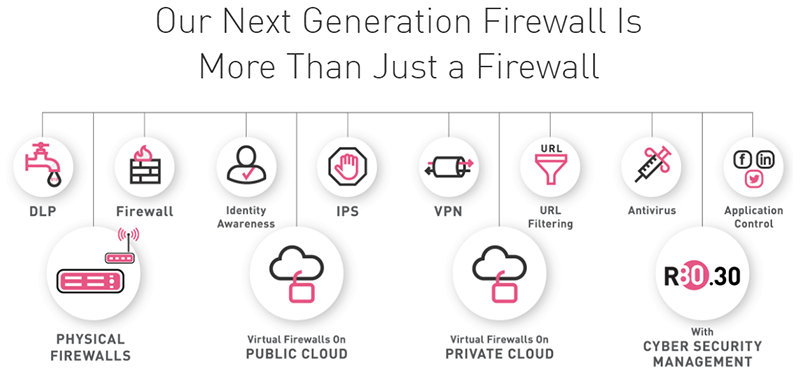
Check Point IPS Software Blade
Delivers complete and proactive intrusion prevention

Intrusion Prevention Systems detect or prevent attempts to exploit weaknesses in vulnerable systems or applications, protecting you in the race to exploit the latest breaking threat. Check Point IPS protections in our Next Generation Firewall are updated automatically. Whether the vulnerability was released years ago, or a few minutes ago, your organization is protected.
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
Click here to jump to more pricing!
Please Note: All Prices are Inclusive of GST
Overview:
Intrusion Prevention Systems detect or prevent attempts to exploit weaknesses in vulnerable systems or applications, protecting you in the race to exploit the latest breaking vulnerability. Check Point Intrusion Prevention System (IPS) provides complete, integrated, next generation firewall intrusion prevention capabilities at multi-gigabit speeds with high security effectiveness and a low false positive rate. IPS protections in our Next Generation Firewall are updated automatically. Whether the vulnerability was released years ago or today, your organization is protected.
Our defense in depth approach combines signatures, protocol validation, anomaly detection, behavioral analysis, and other methods to provide the highest levels of network IPS protection. Check Point IPS provides complete threat coverage for vulnerabilities in clients, servers, operating systems and widely available applications such as PDF readers and browsers that are the preferred targets of threat actors.

Secure
Check Point IPS delivers thousands of signature and behavioral preemptive protections
Efficient
Our acceleration technologies let you safely enable IPS. A low false positive rate saves your staff valuable time
Unified
Enable IPS on any Check Point security gateway reducing Total Cost of Ownership
Online attacks and malware have been evolving, using sophisticated and even evasive attack methods. Check Point addresses the changing threat landscape while meeting several key operational requirements for Intrusion Prevention Systems. Check Point IPS protections include checks for protocol and behavioral anomalies which means we detect vulnerabilities in well-known protocols such as HTTP, SMTP, POP, and IMAP before an exploit is found.
Check Point IPS protects you with:
- Detection and prevention of specific known exploits, for example protection from specific CVEs
- Detection and prevention of DNS tunneling attempts indicating data leakage or evasion
- Detection and prevention of generic attack types without any pre-defined signatures
- Detection and prevention of protocol misuse which may indicate malicious activity
Benefits:
Next-generation security prevention, protection and performance
- Industry-leading IPS and firewall-as tested NSS Labs-delivers 1,000s of signature, behavioral and preemptive protections
- Check Point is ranked #1 in Microsoft and Adobe threat coverage
- Combines with best-of-breed firewall, application control, URL filtering, DLP and more on the most comprehensive, network-class next gen firewall
Unrivaled, multi-Gigabit performance in an integrated IPS
- Up to 15 Gbps of IPS and 30 Gbps of firewall throughput
- Stateful Inspection and SecureXL technology deliver multi-tier IPS inspection and accelerated IPS throughput
- CoreXL technology provides the most efficient and high-performance use of multi-core technologies
Lowest TCO and fastest ROI of any enterprise-class firewall solution
- One-click activation of IPS and firewall protection on any Check Point gateway
- Delivers unmatched extensibility and flexibility-all without adding CapEx
- Integrated into Check Point Software Blade Architecture for on-demand security
Features:
Preemptive Security Updates
Patching is an incomplete security measure, which can leave your network open for attack. By taking a more comprehensive approach, which combines robust IPS functionality with a concerted patching strategy, network administrators can better equip themselves to handle ‘Patch Tuesdays’ and secure the network between upgrades and patches. Let your Check Point Next-Gen Firewall do the security updates for you. Virtual patching is seamless when protections are updated automatically every 2 hours on the Check Point management server and security gateways. In addition new protections are flagged for follow-up ensuring admins stay on top of any changes to their IPS policy.
Painless Deployment
Reduce deployment time and costs by leveraging existing security infrastructure. Optional detect-only mode sets all your existing protections to only detect, but not block, traffic to allow you to evaluate your profile without risking disruption. Simply enable IPS on your existing Check Point Next Generation Firewall. IPS is included in the NGFW package. Want protection from more advanced zero-day and threats in files? Enable antivirus, Anti-bot and SandBlast (sandboxing) Zero-day protection. IPS is also included in the Next Gen Threat Prevention and the SandBlast packages.
Predefined default and recommended profile settings allows for immediate and easy out-of-the-box use with profiles tuned to optimize security or performance.
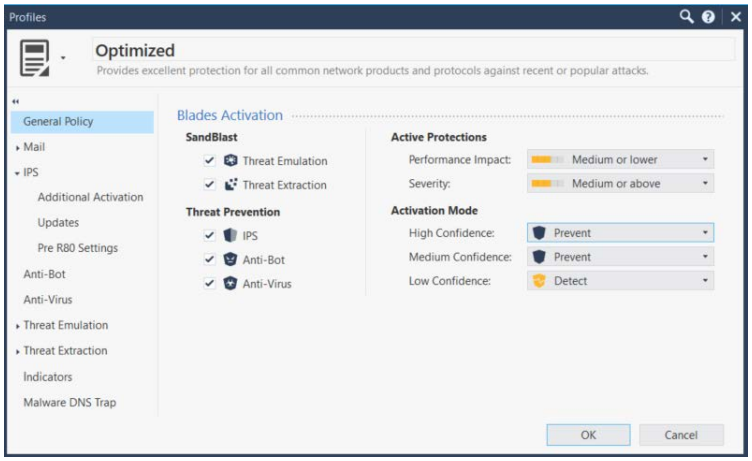
Each protection is described with 3 attributes; Severity, Confidence and Performance Impact. Protection profiles allow administrators to define signature and protection activation rules that match the security needs of their network assets.
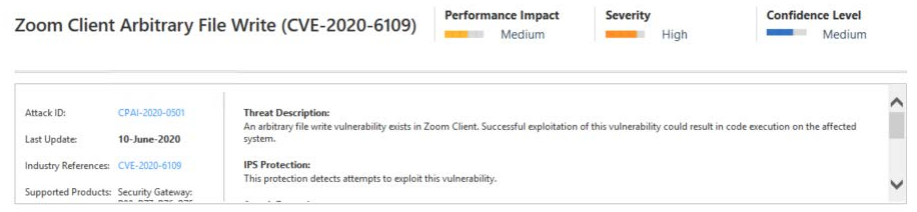
Severity
The Common Vulnerability Scoring System is an open industry standard for assessing the severity of computer system security vulnerabilities where scores range from 0 to 10, with 10 being the most severe. Similarly Check Point assigns a severity level to each IPS protection.
Confidence Level
Some attack are less severe than others, and legitimate traffic may sometimes be mistakenly recognized as a threat, also known as a false positive. The confidence level value is an estimate of how well a protection can correctly recognize a specific attack.
Performance Impact
Some protections require the use of more resources or apply to common types of traffic, which adversely affects the performance of the gateways on which they are activated. This attribute enables better management of the performance of your NGFW.
Unified Threat Management
IPS is configured and managed through a single Check Point management interface. This includes tightly integrated event management. Achieve an unmatched level of visibility to detect and prevent threats. Check Point IPS seamlessly integrates with SmartEvent enabling SOC (Security Operations Center) staff to respond to the highest priority events first, saving them time.
Track events through detailed reports and logs of what is most important to simplify threat analysis and reduce operational overhead. Customizable reports provide easy monitoring of critical security events associated with your business-critical systems. Directly from the security event, go to the associated protection, create an exception or view packet captures.
IPS Tags
In addition to severity, confidence and performance impact you can also activate and deactivate IPS protections using these attributes or tags; vendor (400+), product (600+), threat year, file type, protocol and the effect of the vulnerability such as information disclosure and DoS. This allows security administrators to create an IPS policy that better fits their environment. Profiles and protection attributes greatly simplify management of over 8,000 IPS protections. In your security logs there is a wealth of information about your organization. This includes newly installed applications that may be vulnerable. Analysis will identify these applications and you can then use an IPS tag to activate IPS protections to virtually patch any vulnerable applications found.
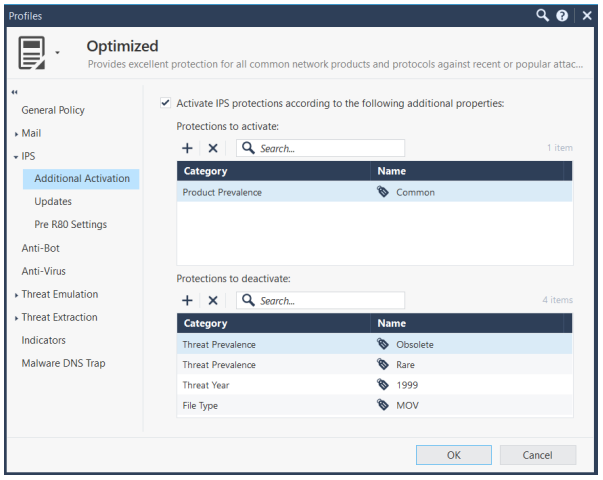
IPS Best Practices
SmartEvent pre-defined views reveals IPS protections in Detect mode that can safely be moved to prevent mode. Most important are the ones where a detect event occurred, but the connection was not prevented by the IPS because of the Detect setting. IPS security best practice number one is to follow up on these events.
Scalable Tbps IPS Performance
Check Point was the first to exploit the performance capabilities of industry standard multi-core processors for IPS, bringing intelligent load-balancing among cores to enable fast, fully-integrated IPS functions in one firewall. Now with Maestro Hyperscale network security, customers can distribute load across multiple Check Point firewalls in N + 1 clusters to achieve over a Terabit per second of IPS throughput. With Check Point IPS technologies, you can have confidence that your organization’s network will get top performance and full functionality without compromising on security.
Specifications:
| Performance | |
|---|---|
| Integrated IPS Performance | Up to 15 Gbps |
| Gateway Load Threshold | Protect firewall performance under load through a configurable software bypass |
| Security | |
| Multi-Method Detection Engine |
Vulnerability and exploit signatures |
| Microsoft Vulnerability Coverage | #1 for Microsoft protections |
| Patch Process Reinforcement | Protect your network from attack while vendor patches are being applied |
| Real-Time Protection |
Protection updates for:
|
| Application Intelligence | Application protections and controls including Instant Message and Peer-to-Peer |
| Open Signatures | Create your own signatures with an open signature language |
| DoS Mitigation Engine | Expanded protections against denial-of-service attacks |
| Deployment | |
| Profiles | Save administrative overhead by assigning the same protections to groups of assets |
| Predefined Profiles | Out-of-the-box protection profiles optimized for security or performance |
| Detect-Only Mode | Set your existing protections to detect, but not block malicious traffic |
| Sandbox New Protections | Provide a 'sandbox' environment to try out new protections without impacting your network |
| Management | |
| Activation Rules |
Activate protections according to:
|
| Packet Capture | Gather traffic data for deep forensic analysis |
| Follow-up | Flag protections for later analysis |
| Timeline View | Easily configure custom views of only what's important to you (e.g., security events associated with your critical network assets) |
| System Overview | IPS system status at-a-glance |
| Unified Management | Manage integrated and dedicated IPS from one interface |
| Network Exceptions | Make exceptions to protections |
| More Protection Information |
Give detailed information on each protection, including:
|
Documentation:
Download the Check Point Intrusion Prevention Systems Datasheet (PDF).
Pricing Notes:
- All Prices are Inclusive of GST
- Pricing and product availability subject to change without notice.
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote

