
Check Point DDoS Protector 60 Appliance
DDoS Protection and Attack Mitigation
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Overview:
Modern DDoS attacks use new techniques to exploit areas that traditional security solutions are not equipped to protect. These attacks can cause serious network downtime to businesses who rely on networks and Web services to operate. DDoS Protector Security Appliances and Cloud DDoS Protection Services block destructive DDoS attacks before they cause damage.

Zero Day DDoS Protection
Blocks a wide range of attacks with customized multi-layered protection

Smart SSL Attack Mitigation
Hardware-based SSL engines inspect the latest SSL/TLS standards

On Premises and Cloud-based Mitigation
Defense Messaging between devices provides accurate and instant mitigation
In today’s info-security threat landscape, denial-of-service and distributed denial-ofservice (DoS/DDoS) attacks are a major cause of network downtime. Whether executed by hacktivists to draw attention to a cause, fraudsters trying to illegally obtain data or funds, or a result of geopolitical events, DDoS attacks are a destructive cyber weapon. Governments, utilities, financial services and commercial institutions face daily attacks.
Preparing for “common” DDoS attacks is no longer enough. Thanks to the growing array of online marketplaces, it is now possible for hackers to wreak havoc with virtually no knowledge of computer programming or networks. Attack tools and services are easy to access, making the pool of possible assaults larger than ever.
With Burst attacks and Advanced Persistent DDoS campaigns, hackers launch multivector, blended campaigns with high volume network vectors with more sophisticated application-layer attacks. In addition, recent IoT threats spawned the largest DDoS attack in history, propelling the industry into the 1Tbps DDoS era.
With these new threats, it is critical to ensure your DDoS mitigation solution can protect your organization and customers from today and tomorrow’s sophisticated attacks.
Key Features
- Full protection of data center applications against emerging network threats
- Maintain network performance even when under high PPS network attacks
- Maintain excellent user response time even under attack
- DDoS Protector combines intrusion prevention system (IPS), network behavioral analysis (NBA), denial-ofservice (DoS) protection and SSL attack protection
Key Benefits
- Get the most accurate attack detection and prevention without blocking legitimate user traffic
- Reduce Total Cost of Ownership (TCO) of Security Management
- Multitude of security tools in a single box
- Single management application to manage multiple DDoS Protector units cross multiple data centers
- Full investment protection and extended platform life time with payas-you-grow license upgrade scalability delivering best ROI and CAPEX investment protection
Why DDoS Protector?
DDoS Protector includes a comprehensive set of four essential security modules - anti-DDoS, network behavioral analysis (NBA), intrusion prevention system (IPS) and SSL-attack protection - to fully protect the application infrastructure against known and emerging network security attacks. It employs multiple detection and mitigation modules, including adaptive behavioral analysis, challenge response technologies and signature detection.
Compared to standalone solutions, the synergy of multiple security modules on a single, hardware-accelerated platform enables effective protection against attackers who seek to systematically compromise business assets while providing unified reporting, forensics and compliance.
DDoS Protector consists of adaptive, behavioral-based real-time signature technology that detects and mitigates emerging network attacks, zero-day, DoS/DDoS, application misuse attacks, network scanning and malware spread. It eliminates the need for human intervention and does not block legitimate user traffic.
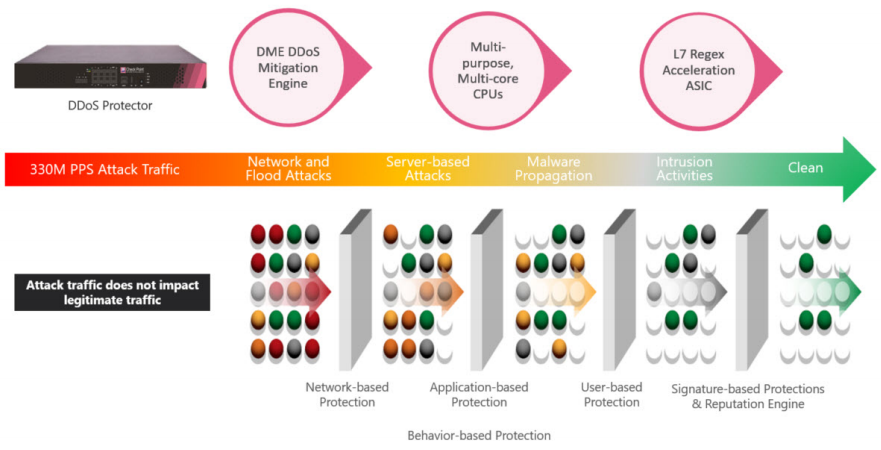
Features:
Integrated on Premises and Cloud DDoS Protection
DDoS Protector is part of Check Point’s Attack Mitigation Solution and is an awardwinning, real-time, perimeter attack mitigation device that secures organizations against emerging network and applications threats. DDoS Protector protects the infrastructure against network and application downtime (or slow time), application vulnerability exploitation, malware spread, network anomalies, information theft and other types of attacks.
DDoS Protector provides the industry’s most advanced, automated protection from fastmoving threats, including from recent IoT based attacks such as Mirai. It is uniquely built to overcome both the complexity and scale of today’s sophisticated IoT-based botnets. DDoS Protector also helps organizations win the ongoing security battle against availability attacks, by detecting and mitigating known and zero-day DoS/DDoS attacks in real-time. It protects against other security threats that are usually undetected by traditional DDoS mitigation tools, such as SSL-based flood attacks, attacks on login pages and attacks behind CDNs.
With DDoS Protector, Check Point’s attack mitigation solution offers protection with the shortest mitigation time and broadest attack coverage. Check Point provides a hybrid solution combining on premise and cloud-based mitigation tools in a single integrated solution, designed to optimally block multiple attack vectors occurring in parallel.
A DDoS Protector Security Appliance to Fit Your Every Need
The DDoS Protector appliances offer versatile connectivity and mitigation capacities, adhering to enterprise and service provider deployments. Bandwidth mitigation capacities range from 6, all the way up to 400 Gbps. Protection can be further augmented with our Cloud DDoS Protector Services.
Deployment Modes
DDoS Protector can be deployed inline, out-of-path (OoP) or in a scrubbing center to provide the highest mitigation accuracy within the shortest time. Each deployment mode offers the same performance as an inline device.
With DDoS Protector deployed either inline or out-of-path as well as in a scrubbing center, the devices are able to communicate with each other in real-time to collect automatic updates of normal traffic baselines, detect behavioral patterns and obtain attack footprints. This constant real-time flow of Defense Messaging enables DDoS Protector to provide accurate and instant mitigation without the need to learn this information when an attack occurs.
Deploying DDoS Protector devices out-of-path or in a scrubbing center is the most scalable and flexible solution as it is based on the maximum attack mitigation capacity needed, without being limited by the actual network physical topology.
Integrated, Hybrid Solution
In addition to the security modules integrated in DDoS Protector, Check Point’s Attack Mitigation Solution (AMS) includes an SSL decryption/encryption engine, a WebApp Protector module and Hybrid Cloud DDoS Protector Service that works in sync with the on premises solution. With no performance impact or risk, Check Point’s AMS ensures business continuity even when under attack.
The solution is enhanced with a central Security Information Event Management (SIEM) to provide unified situational awareness to our Emergency Response Team (ERT). Unique messaging assures that each component provides information about traffic baselines and real-time signatures to the others, so that all system components have full visibility into all information.
Through this messaging, Check Point’s AMS can detect attacks where it should and mitigate attacks where it’s best. For example, the system can detect a volumetric attack at the network perimeter but mitigate it in the cloud. This automatic, real-time feature enables organizations to scale the mitigation capabilities of the solution by moving mitigation as far as possible from the application infrastructure.
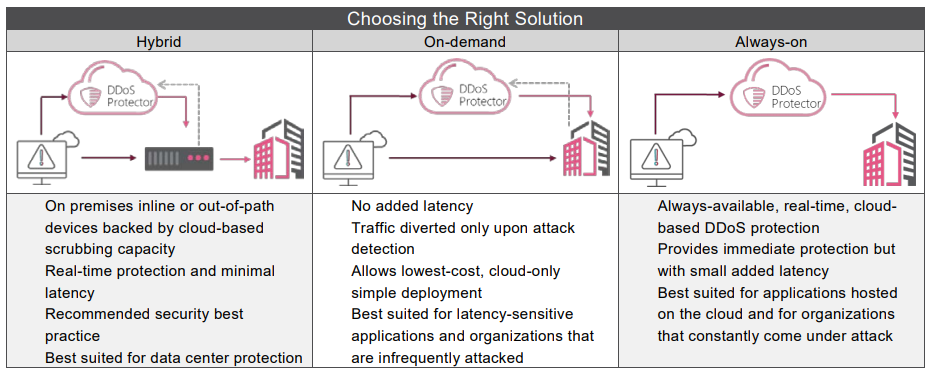
Cloud DDoS Protector Services
Check Point’s DDoS Protector Cloud Service can be delivered in On-demand, Always-on, or in a Hybrid configuration, and can be custom-tailored to suit any customer need, network topology or threat profile.
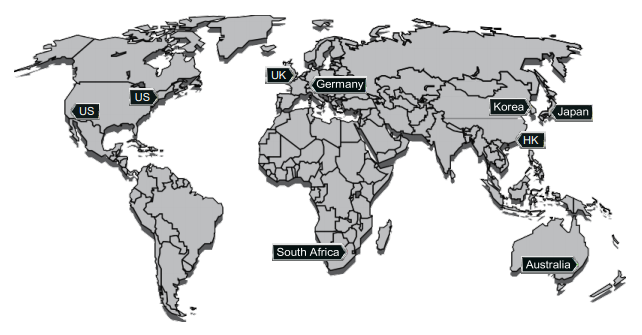
Global Coverage, Massive Capacity
Check Point’s DDoS Protector Cloud Service is backed by a worldwide network of 9 global scrubbing centers, with 3.5 Tbps of mitigation capacity (and growing). Check Point’s scrubbing centers are globally connected in full mesh mode, using Anycastbased routing. This ensures that DDoS attacks are mitigated closest to their point of origin, and provides truly global DDoS mitigation capable of absorbing even the largest volumetric attacks.
Check Point DDoS Protector Cloud Service Features
Our cloud-based service includes the same features you get in the on premises solution. This includes behavioral-based detection using advanced, patented machine-learning algorithms to protect against known and unknown threats, zero-day protection against network and application layer DDoS attacks such as Burst attacks, DNS attacks and others. Our unique protection against SSL-based attacks does not add latency or require customers provide full SSL certificates. Our extensive compliance options and certification are unparalleled by any rival and include industry-specific certifications such as PCI and HIPAA, as well as cloud security standards such as ISO 27001, ISO 27017, ISO 27018, ISO 27032 and others.

Expert Support
The Emergency Response Team (ERT) is a group of security experts that provides 24x7 support and mitigation services for customers facing a broad array of application and network layer DDoS attacks. The ERT compliments an organization’s ability to deal with cyber-attacks by leveraging both security expertise and real-time threat intelligence services. The team engages in mitigating a broad array of security events, including malware outbreaks, application exploits, DDoS attacks and DoS attacks. The ERT provides the required expertise and service during prolonged, complex attacks and helps to quickly restore the operation by mitigating DDoS attacks fast.
Easy Management and Control
Absolute Vision is a unified management and monitoring system. It provides advanced element management capabilities through a unique plug-and-play device support mechanism, including initial device setup, on-going maintenance, SSL certificate management, real-time reporting, capacity utilization measurement, forensics, task scheduling and more. It provides automation of monitoring and maintenance processes across all the devices it manages and includes a central repository of vital device information for IT managers to easily find hardware platform details, upgrade and software version management, and installed licenses. As a result, continuous service delivery through the entire device’s operational life cycle is ensured. A REST API is available for SIEM integrations.
Technical Specifications:
| Model | 6 | 20 | 60 | 110 | 200 | 220 | 400 |
|---|---|---|---|---|---|---|---|
| Network Grade | Enterprise Grade | Ultra High End | |||||
| Performance | |||||||
| Max Mitigation Capacity/ Throughput (Gbps) | 6 | 20 | 60 | 110 | 200 | 220 | 400 |
| Max Attack Concurrent Sessions | Unlimited | Unlimited | Unlimited | Unlimited | Unlimited | Unlimited | Unlimited |
| Max DDoS Flood Attack Prevention Rate (PPS) | 5.8M | 25M | 25M | 50M | 330M | 146M | 330M |
| SSL/TLS CPS (RSA 2K) | 20K | 95K | 95K | 150K | - | 150K | - |
| Latency | < 60 micro seconds | ||||||
| Operation Mode | |||||||
| Network Operation | Transparent L2 Forwarding/IP Forwarding | ||||||
| Deployment Modes | In-line; SPAN Port Monitoring; Copy Port Monitoring; local out-of-path; Out-of-path mitigation (scrubbing center solution) | ||||||
| Tunneling Protocol | VLAN Tagging, L2TP, MPLS, GRE, GTP, IPinIP | ||||||
| IPv6 | Yes | ||||||
| Jumbo Frame | Supported | ||||||
| Inspection Ports | |||||||
| 10/100/1000 Copper Ethernet | 6 | - | - | - | - | - | - |
| 1/10 Gigabit Ethernet (QSFP+) | 2 | 24 | 24 | 24 | 20 | 24 | 20 |
| 40 Gigabit Ethernet (QSFP+) | - | - | - | 4 to 8 | 4 | 4 to 8 | 4 |
| 100 Gigabit Ethernet (QSFP28) | - | - | - | 0 to 4 | 4 | 0 to 4 | 4 |
| Physical | |||||||
| Enclosure | 1U | 2U | 2U | 2U | 2U | 2U | 2U |
| Standard (W x D x H) | 17.2 x 16 x 1.7 in. | 17.2 x 18.9 x 3.5 in. | 17.2 x 18.9 x 3.5 in. | 19 x 21.6 x 3.5 in. | 16.7 x 23.6 x 3.5 in. | 19 x 21.6 x 3.5 in. | 16.7 x 23.6 x 3.5 in. |
| Metric (W x D x H) | 436 x 406 x 44 mm | 436 X 480 X 88 mm | 436 X 480 X 88 mm | 482 x 550 x 87 mm | 424 x 600 x 88 mm | 482 x 550 x 87 mm | 424 x 600 x 88 mm |
| Weight | 7 Kg (15.4 lbs.) | 11.2 kg (24.7 lbs.) | 11.2 kg (24.7 lbs.) | 14.5 kg (31.9 lbs) | 18.7 kg (41.2 lbs.) | 14.5 kg (31.9 lbs) | 18.7 kg (41.2 lbs.) |
| Power | |||||||
| Dual, Hot-Swappable PSU | Optional | Included | Included | Included | Included | Included | Included |
| Power Inpu | AC 100 ~ 120V, AC 200 ~ 240V @ 47 ~ 63Hz, DC: -36 - -72V | ||||||
| Power Consumption | 140W | 320W | 320W | 550W | 890W | 550W | 890W |
| Heat Dissipation | 477 BTU/h | 1091 BTU/h | 1091 BTU/h | 1880 BTU/h | 3037 BTU/h | 1880 BTU/h | 3037 BTU/h |
| Environment Conditions | |||||||
| Operating Environment | 32o to 104o F / 0o to 40o C, 5~95% Humidity (non-condensing) | ||||||
| Certifications | |||||||
| Safety | cTUVus, EN/IEC 60950-1 (CB), CCC, IEC 60950-1, GB4943, CNS 14336 | ||||||
| Emissions |
USA Title 47 Part 15; EMC 2014/30/EU; LVD 2014/35/EU; FCC Part
15B (Class A); CS03; ETSI EN 300 386 V2.1.1 (2016-07); EN
61000‒3‒2, EN 61000‒3‒3, AS/NZS CISPR 32, Brazil ANNEX TO RES Nº 442, Japan V2/2015.04 & V-3/2015.04, China GB 9254-2008, Russia CU TR 020 2011, Korea KN 32/35, Taiwan CNS 13438 |
||||||
| Environment | RoHS II (EU directive 2011/65/EU | ||||||
Documentation:
Download the Check Point DDoS Protector Appliances Datasheet (PDF).
Pricing Notes:
- All Prices are Inclusive of GST
- Pricing and product availability subject to change without notice.
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote
Our Price: Request a Quote


