
Check Point CloudGuard Cloud Intelligence and Threat Hunting

Check Point CloudGuard Cloud Intelligence and Threat Hunting
Contact us for Pricing!
Get a Quote
- Robust logs enrichment engine
- Cloud intrusion alerts
- Visual exploration tool
- Firehose connector into 3rd party SIEM
- Threat Cloud and CloudBots integration
- A turnkey solution that integrates with your cloud infrastructures
Overview:
Check Point CloudGuard Cloud Intelligence and Threat Hunting, part of the CloudGuard Cloud Native Security platform, provides cloud native threat security forensics through rich, machine learning visualization, giving real-time context of threats and anomalies across your multi-cloud environment.
![]()
Multi Cloud Threat Hunting
Detect activity anomalies leveraging machine learning and threat research
![]()
Auto Remediation
Intuitive visualization, querying, intrusion alerts, and notifications
![]()
Actionable Intelligence
CloudBots for rapid remediation for misconfigurations and drift
Cloud Intelligence and Threat Hunting
Advanced cloud security intelligence, contextualized visualization of threats, and actionable security insights- learn how incidence response and forensics can further enhance your security posture across your multi-cloud environments.
Advanced Multi-Cloud Security Monitoring and Analytics
CloudGuard delivers advanced security intelligence, including cloud intrusion detection, network traffic visualization, and cloud security monitoring and analytics. Its object-mapping algorithms combine cloud inventory and configuration information with real-time data monitoring from a variety of sources from Amazon AWS, Microsoft Azure and Google Cloud native log, packet capture appliance, and alert tools.
The outcome is rich contextualized information, enhanced and simplified visualization, deep event correlation, querying, intrusion alerts and notifications of policy violation, enhancing Security Operation Centers (SOC) with relevant cloud security intelligence for faster and more efficient incident response.
Features:
Transforming Logs into Security Logic
CloudGuard provides cloud-native threat protection and security intelligence for the public cloud. CloudGuard enriches cloud logs with context, transforms them into readable security logic, and enables security teams to take cloud security to the next level.
Using CloudGuard businesses can:
- See every data flow and audit trail in today’s elastic cloud environments
- Make sense of cloud data and activities to expedite investigation processes
Cloud Security will never look the same
CloudGuard delivers cloud intrusion detection, network traffic visualization and user activity analytics. Its object-mapping algorithms combine cloud inventory and configuration information with real-time monitoring data from a variety of sources including VPC Flow Logs, CloudTrail, Amazon GuardDuty, AWS Inspector, as well as Check Point’s Threat Cloud feeds, IP reputation and geo databases.
The outcome is rich contextualized information that is used within the CloudGuard platform for enhanced visualization, querying, intrusion alerts and notifications of policy violations. It can also be piped to third-party SIEM solutions, anywhere.
With robust threat detection at core, CloudGuard CloudBots technology also extends remediation capabilities indefinitely - allowing you to create custom response to any type of network alert, audit trail, or any other.
CloudGuard is the only platform that attributes network traffic to cloud-native ephemeral services such as Amazon Lambda functions as well as other cloud-native platform components (RDS, Redshift, ELB, ALB, ECS) to provide a complete view and understanding of your cloud infrastructure across time.
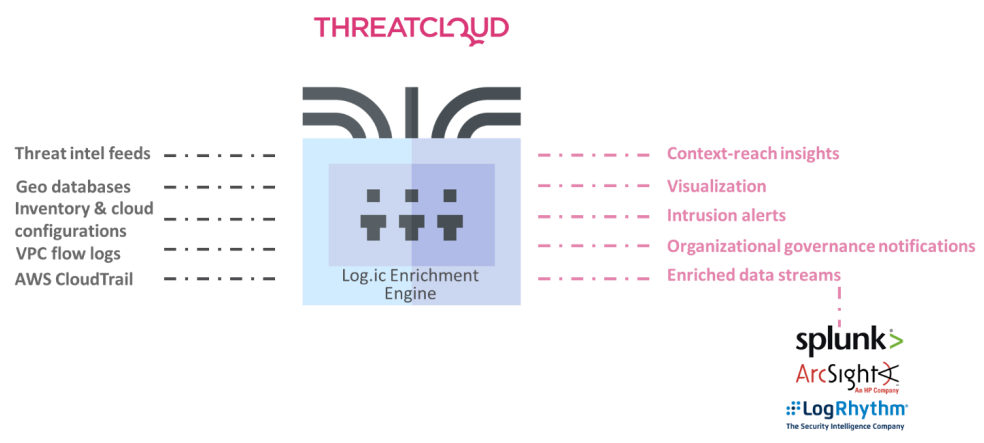
Detect and prevent cloud anomalies using AI, alert and quarantine threats with Check Point's Threat Cloud
CloudGuard for Cloud Intelligence and Threat Hunting uses security best practices of signature detection, built-in rules, threat intelligence feeds and existing traffic flow to create a baseline of your network and user activity. It also uses AI and anomaly detection algorithms to spot potentially unauthorised or malicious activity within your cloud environments, including serverless applications. CloudGuard can provide real-time policy violation and intrusion detection alerts based on user-defined criteria to the security admin team.
-
Feeding off of the world’s largest IOC
database:
CloudGuard leverages Check Point’s ThreatCloud to enrich
logs with intelligence from various feeds, including:
- 750M+ malicious hashes, sites and C&C addresses
- 11M behavioral signatures
- 2.5M daily detections o Dozens of external feeds
- Auto-remediation with CloudBots: CloudBots is a serverless framework that triggers a remediation function with a single click deployment, running entirely within your environment. Add CloudBots to create custom response to any type of network alert, audit trail, or other, and remediate threats at once with CloudGuard.
Expedite Investigation Processes with Big Data Analytics
CloudGuard includes a visual exploration tool that allows you to analyze the network activity and traffic traversing in and out of your cloud environment. You can choose from an extensive set of predefined queries or craft custom ones using CloudGuard's expressive yet concise query language. The Explorer visualization feature lets you see every element and traffic in your VPC at a glance, and from there, zoom into the relevant entity or connection. Use CloudGuard’s rich contextualized visualization to fire: Deep investigation, Incident response, and Threat Hunting.
Enrich your SIEM to see the cloud
CloudGuard Log.ic’s firehose connector feeds the enriched log traffic in a highly contextualized JSON format to various SIEM products for further investigation. Pipe into Splunk, ArcSight, LogRythm and more, to nurture with critical data on ephemeral as sets and security posture awareness.
Use Cases:
Cloud Threat Intelligence
CloudGuard ingests cloud native log and event data, delivering contextualized visualization of entire public cloud infrastructure and cloud security analytics, helping to enhance:
- Real-time intrusion detection and policy violation alerts based on user-defined criteria
- Comprehensive investigation of security threats with cloud network security analytics, streaming the world’s largest security intelligence database, ThreatCloud.
- Continuous extended threat prevention with CloudBots and advanced encryption
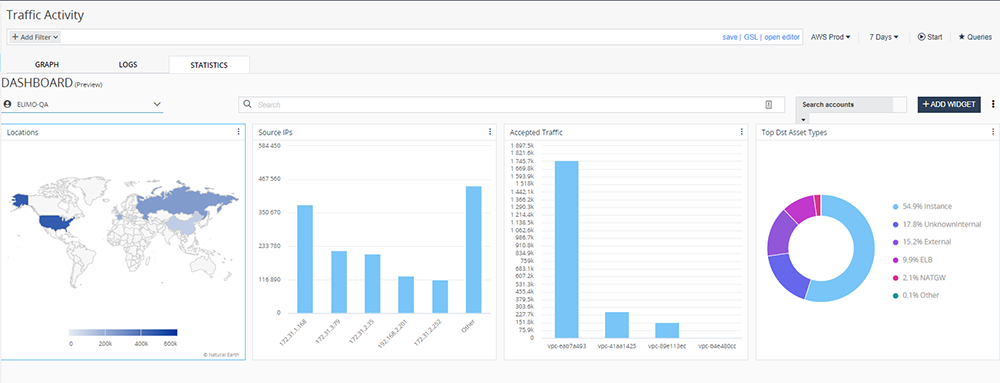
Forensics and Threat Hunting
CloudGuard ingests cloud native log and event data, delivering contextualized visualization of entire public cloud infrastructure and cloud security analytics, helping to enhance:
- Incident Response (Cloud Forensics): Alerts on network activity and account behaviors
- Network Troubleshooting: Real-time configuration and traffic monitoring in the VPC and VNET, including ephemeral services and cloud-native platform components from Amazon AWS, Microsoft Azure, and Google Cloud Platform.
- Compliance: Instant notifications on regulatory violations and ace audits
- Compliance: Instant notifications on regulatory violations and ace audits
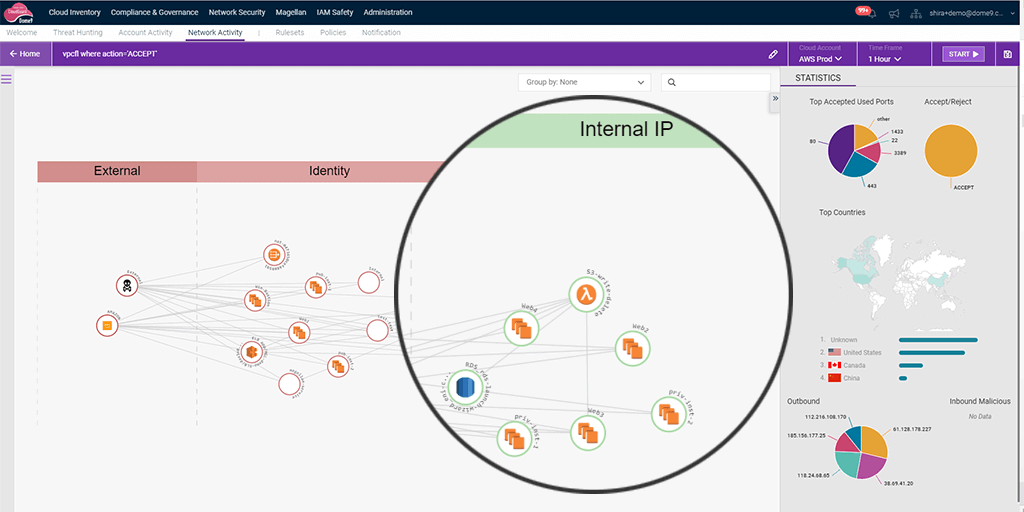
Superior Automation and SIEM Integration
Advanced cloud security monitoring automation and Event Management (SIEM), for critical insights and integration of cybersecurity tools, and robust and seamless defense.
- Precise and smooth integration with third party SIEM solutions
- Comprehensive visibility of contextualized logs into ephemeral assets and security posture awareness
- CloudGuard feeds critical insights to SIEM solutions for further investigation.
CloudGuard includes out-of-the-box integrations with leading SIEM vendors, making integrating IT and security technologies easy, fast, and flexible.

Documentation:
Download the Check Point CloudGuard Cloud Intelligence and Threat Hunting Datasheet (PDF).
Pricing Notes:
- All Prices are Inclusive of GST
- Pricing and product availability subject to change without notice.
Our Price: Request a Quote

