
Check Point Application Control Software Blade
The industry's strongest application security and identity control
to organizations of all sizes

Check Point Application Control provides the industry's
strongest application security and identity control to
organizations of all sizes. Integrated into the Check Point
Infinity Architecture, Application Control enables IT teams to
easily create granular policies based on users or groups-to
identify, block or limit usage of applications and widgets.
Applications are classified into categories, based on diverse
criteria such as applications' type, security risk level,
resource usage, productivity implications and more.
Overview:
Check Point Application Control provides the industry's strongest application security and identity control to organizations of all sizes. Integrated into the Check Point Infinity Architecture, Application Control enables IT teams to easily create granular policies based on users or groups-to identify, block or limit usage of applications and widgets. Applications are classified into categories, based on diverse criteria such as applications' type, security risk level, resource usage, productivity implications and more.

Granular
Granular control of social networks, applications and application features - identify, allow, block or limit usage
Widespread
Leverages the world's largest application library, grouping apps into categories to simplify policy creation and protect against threats and malware

Integrated
Integrated into the Check Point Infinity Architecture to provide centralized management of security policy via a single console
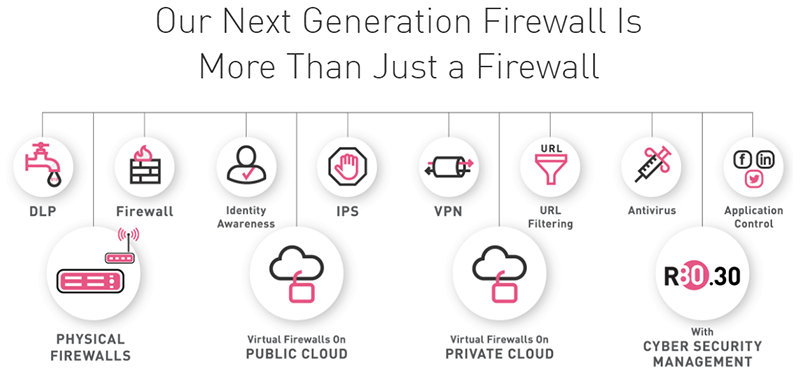
Benefits:
Granular application control
- Identify, allow, block or limit usage of thousands of applications by user or group
- UserCheck technology alerts users about controls, educates on Web risks, policies
- Embrace the power of Web Social Technologies and applications while protecting against threats and malware
Largest application library with AppWiki
- Leverages the world's largest application library with over 250,000 Web applications and social network widgets
- Identifies, detects, classifies and controls applications for safe use of Web social technologies and communications
- Intuitively grouped in over 80 categories-including Web, IM, P2P, Voice & Video and File Share
Integrated into Check Point Software Blade Architecture
- Centralized management of security policy via a single console
- Activate application control on any Check Point security gateway
Features:
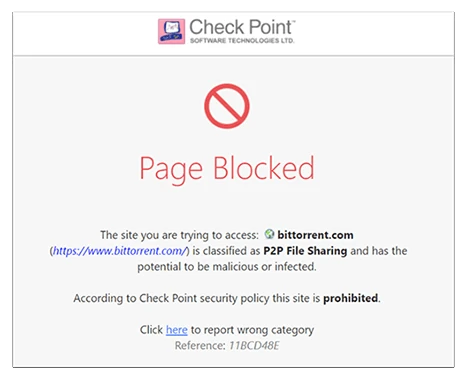
Application Detection and Usage Control
Enables application security policies to identify, allow, block or limit usage of thousands of applications regardless of port, protocol or evasive technique used to traverse the network. Combined with Identity Awareness, IT administrators can create granular policy definitions. User and group application usage is controlled according to user or group needs and applications' characteristics in terms of security, productivity and resource utilization.
Inspect SSL/TLS Encrypted Traffic
Equipped with Check Point's SSL inspection technology, Application Control scans and secures SSL/TLS encrypted traffic passing through the gateway. Organizations can granularly define exceptions for SSL/TLS inspection to protect user privacy and comply with corporate policy.
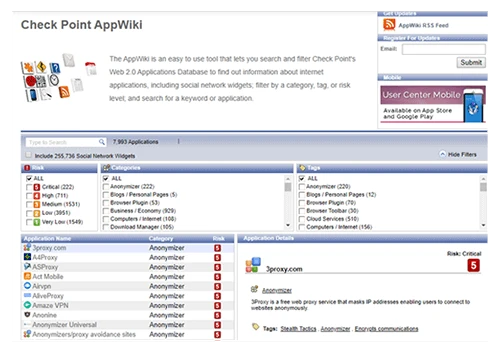
AppWiki Application Classification Library
To support the dynamic nature of Internet applications, the Application Control database is continuously and automatically updated. AppWiki enables application scanning and detection of nearly 8,000 distinct applications and over 250,000 Web widgets including:
- Instant messaging
- Social networking
- Video streaming
- VoIP
- Games
Integrated into the Check Point Infinty Architecture
Application Control is integrated into the Check Point Infinty Architecture. It can be easily and rapidly deployed on existing Check Point Security Gateways, saving time and reducing costs by leveraging existing security infrastructure.

Specifications:
| Supported Appliance Families | |
|---|---|
|
|
| Supported Operating Systems | |
|

