The Latest Check Point News
Product and Solution Information, Press Releases, Announcements
| Blueprint For Securing Industrial Control Systems | |
| Posted: Thu Nov 14, 2019 07:48:12 AM | |
|
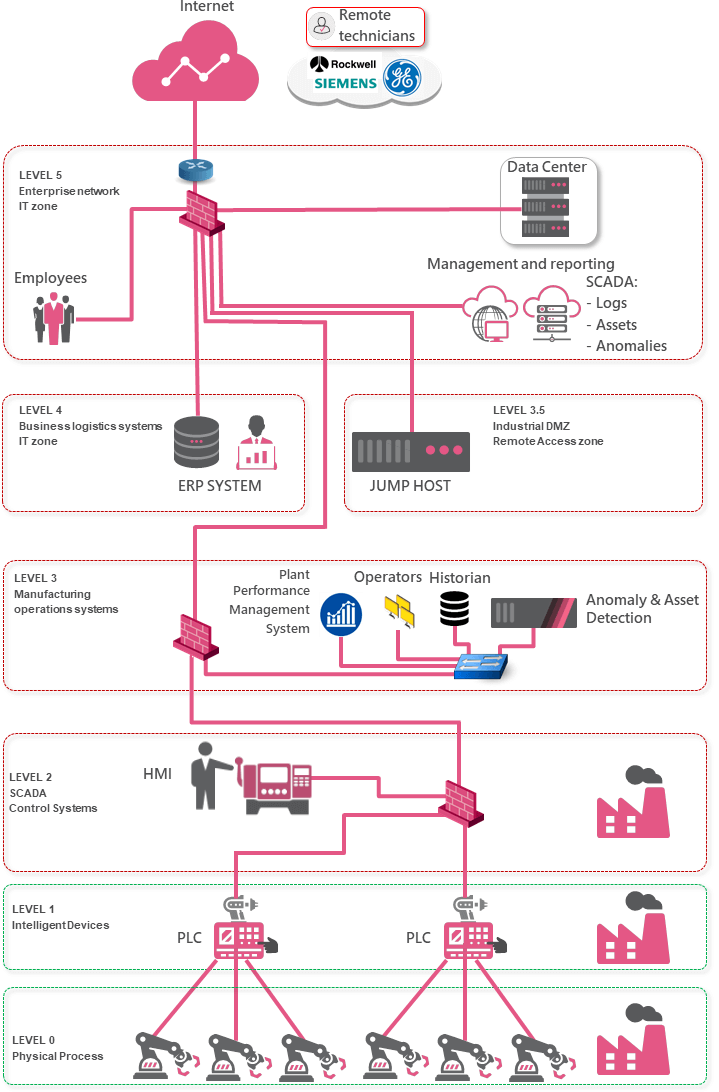
In order to secure Critical Infrastructure environments, it is vital to keep a holistic view and look at every part of the network, both the IT and OT parts and investigate the systems and processes in each zone, analyze the attack vectors and risk and provide recommended security controls. In order to do so, we use the Purdue model, which was adopted from the Purdue Enterprise Reference Architecture (PERA) model by ISA-99 and used as a concept model for Computer Integrated Manufacturing (CIM). [3] It is an industry adopted reference model that shows the interconnections and interdependencies of all the main components of a typical Industrial Control System, dividing the ICS architecture into 3 zones and subdividing these zones into 6 levels. Applying Security to ICS should dissect the 6 different Purdue layers and how they map to different areas in the network. The idea is to explain the communication flows between the different levels in the Purdue model and how they should be secured. The following drawing is a high-level representation of a typical IT/OT environment. However, the link between level 2 and 3 may vary depending on the organization type:
Level 5 and 4: The Enterprise IT Network and Business Logistics Systems Recommended Security Controls: As this is the IT network where the users reside and this is where the internet egress point is located, it is recommended to enable the full Next Generation Threat Extraction feature set on the network level:
It is also recommended to install the full Endpoint suite on the usersí machines. Last but not least, it is also very important to secure (public) cloud services as these are usually also connected to corporate resources and therefore also a potential attack vector. Enabling network and endpoint security can prevent and eliminate the attacks prior to breaching the ICS equipment. The SmartCenter is used as a management station for all the security gateways mentioned in this blueprint. Level 3.5: The Industrial DMZ Recommended Security Controls: To ensure maximum availability of the remote access gateway allowing for third parties to remotely manage and monitor the OT equipment, it is vital to protect the gateway with an anti-DDoS solution (preferably on premises and cloud-based). In this blueprint, there is a jump server in the industrial DMZ. The VPN RAS sessions are terminated on the perimeter gateway in level 5. The gateway terminates VPN traffic, scans it for malware and only allows RDP traffic to the jump host. The jump host is then used to connect to operator workstations in level 2 for remote maintenance work. This approach is much safer than allowing inbound L3 VPN connections from the internet straight into level 2 and dramatically reduces the risk of the OT network becoming infected due to unsafe RAS connections originating from third parties. The jump server itself is protected by the gateway, which will only allow inbound RDP and has the necessary security controls enabled such as IPS, Anti bot and application control. Level 3: Manufacturing Operations Systems Recommended Security Controls:
Level 2 and 1: Securing Communications Between Levels Recommended Security Controls:
Level 0: Physical Processes Recommended Security Controls: It is recommended to use point to point connections between the intelligent devices in level 1 and the field devices in level 0. In case the communication between level 1 and level 0 is done over IP, prefer point to point connections. If point-to-point links are not possible and Ethernet switches are used in level 0, ensure the appropriate L2 security is enforced: admin down of all unused switch ports, MAC authentication on used switch ports, consider the use of additional security gateways between Level 1 and Level 0. The use of a trusted baseline policy with the application control blade can warn an admin if an unknown command is sent to a field device. The Check Point components that are offered in this structures:
5 Key Takeaways Here are 5 key takeaways to protect critical infrastructures:
|