
Check Point Identity Awareness Software Blade
The industry's strongest level of gateway security and identity awareness
Check Point Identity Awareness offers granular visibility of users, groups, and machines, providing unmatched application and access control through the creation of accurate, identity-based policies. Centralized management and monitoring allows for policies to be managed from a single, unified console.
Overview:
Check Point Identity Awareness offers granular visibility of users, groups, and machines, providing unmatched application and access control through the creation of accurate, identity-based policies. Centralized management and monitoring allows for policies to be managed from a single, unified console.

Visibility
Increase visibility of user activities with a dynamic user-based policy

Control
Prevents unauthorised access, while still allowing users to work remotely
Easy to Deploy
Enable on any Check Point gateway and integrate with leading identity vendors
The Importance of Access Roles
Role-based access control (RBAC) authorizes requests for network access based on an individual’s defined role. Practicing RBAC results in employees only having access to the information they need to perform their job duties. For example, access to sensitive data is only granted to employees in an organization who require this information in order to perform their specific job duties.
Employing RBAC improves operational efficiency and compliance. When an employee changes job positions, their access to data can be changed with a simple role switch. With clear roles defined, the IT department can clearly see and ensure that only approved roles are accessing sensitive data. Unfortunately, identities and devices are easily compromised. According to Verizon DBIR, 81% of data breaches involve stolen credentials. Security professionals are responding to these threats by shifting to a zero trust security approach where no device, user, workload, or system is trusted by default.
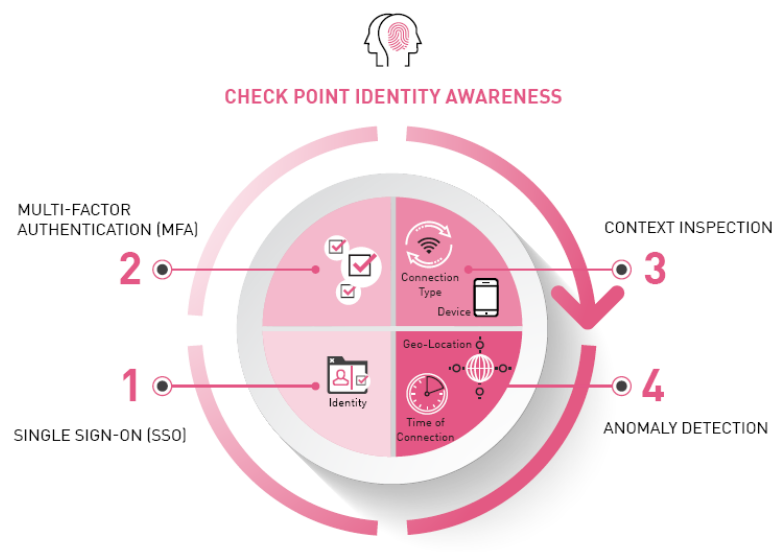
Trust No User or Device
Check Point Identity Awareness seamlessly integrates with leading IAM (Identity and Access Management) vendors to ensure access is only granted to authorised users from devices verified to be secure using anomaly detection and context-aware policies. Multifactor authentication, identity agents and user to IP address mapping from trusted third parties verify the identity of the user and add context to verify the user is connecting from a trusted device.
Benefits:
Increases visibility of user activities
- Centrally manage user access to company resources and Internet applications
- Granular user-, group- and machine-based visibility and policy enforcement
- Easily distinguish between employees and others, i.e., guests and contractors
Improves control of corporate resources
- Granular access to data centers, applications and network segments by user, machine or location
- Prevent unauthorised resource access, while allowing users work remotely
- Prevent threats and data loss by restricting access to resources by users and devices
Easy to deploy in any organization
- Integrated into Check Point Software Blade Architecture
- Provides scalable identity sharing between gateways
- Seamless Active Directory (AD) integration with multiple deployment options-Clientless, Captive Portal or Identity Agent
Features:
Dynamic, User-based Policy
Dynamic, identity-based policy provides granular visibility and control of users, groups and machines and is easier to manage than static, IP-based policy. In a single, unified console administrators define the objects once. When gateways see a connection for the first time, the IP is mapped to the user and group by querying the third party user directory. This dynamic user to IP mapping frees administrators from constantly updating the Check Point policy.
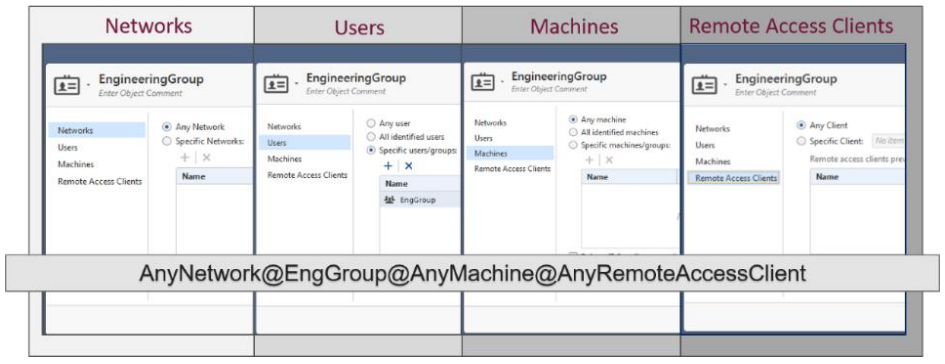
Configurable Access Roles
With Identity Awareness, you can easily add users, user groups, and machine identity intelligence to your security defenses. Unlike traditional firewalls that only use IP addresses to monitor traffic, Identity Awareness monitors traffic while giving your organization insight into user and computer identities. Access Role objects can include networks, users and user groups, machines and machine groups, as well as remote access clients.
Multiple User Identification Sources

Identity Awareness is comprised of multiple identity connectors that obtain identity from a variety of sources.
- Terminal Servers
Identities are acquired using agents installed on a Windows-based application server that hosts Terminal Servers, Citrix XenApp, and Citrix Xen Desktop services. These agents identify individual user traffic coming from Terminal Servers. - Identity Agents
Identities are acquired using agents that are installed on the Endpoint computers. - Active Directory Query
Identities are acquired seamlessly from Microsoft Active Directory WMI API. - RADIUS Accounting
Identities are acquired from a RADIUS accounting client. - Identity Collector
Identities are acquired using a multi-purpose agent installed on a Windows host. The agent uses APIs to connect to Microsoft Active Directory Domain Controllers, Cisco ISE servers, and NetIQ eDirectory LDAP servers. The agent can also parse syslog messages to extract identities from a syslog message. - Identity Web API
Gives you a flexible method for creating identities and easily perform third party integrations
Identity Collector
Identity Awareness maps users and computer identities, allowing you to enforce access and audit data based on identity. The Check Point Identity Collector agent installed on a Windows host acquires identities from: Microsoft Active Directory Domain Controllers via the Windows Event Log API, Cisco Identity Services Engine (ISE) servers via the pxGrid API, and can parse identities from syslog and integrates with NetIQ eDirectory.
Browser-Based Authentication
Another feature of Identity Awareness is the use of browser-based authentication. Identities from unidentified users can be acquired through Captive Portal and Transparent Kerberos Authentication. Captive Portal is a simple method that attempts authentication through a web interface before granting a user access to Intranet resources. Transparent Kerberos Authentication is when a browser attempts to authenticate users transparently by retrieving identity information before a Captive Portal sign-on page pops up. When Transparent Kerberos Authentication is enabled, Captive Portal requests authentication data from the browser itself. If this transparent method is unable to authenticate, then a user must enter their credentials in the Captive Portal sign-on before accessing the resources.
Identity Sharing
Identity Aware Security Gateways can share the identity information that they acquire with other Identity Aware Security Gateways. Users who need to pass through many Security Gateways are only identified once, without creating additional load on the identity sources or interfering with a streamlined end-user experience.
Data Center Integrations
Check Point CloudGuard Controller, Identity Awareness and Check Point security gateways integrate seamlessly within the following virtual cloud environments: Amazon Web Services (AWS), Microsoft Azure, Cisco ACI, Cisco ISE, Google Cloud Platform (GCP), Nuage Networks VSP, OpenStack, VMware vCenter and VMware NSX. CloudGuard Controller scanner periodically polls objects in the data center. The scanner then updates the management server data center objects and Identity Awareness enabled gateways to enforce the security policy.
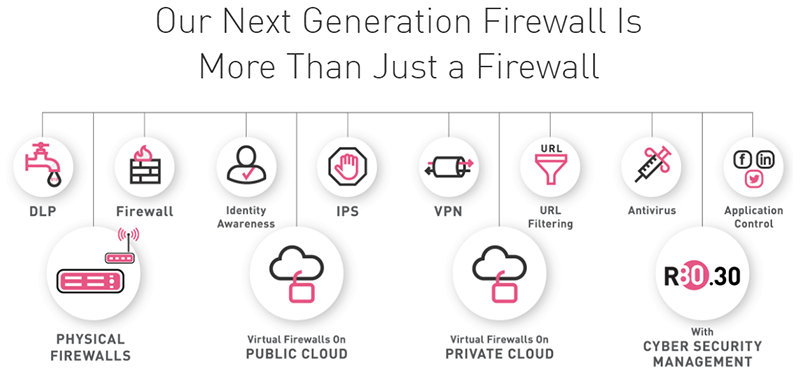
Tightly Integrated Security Ecosystem
Identity Awareness is integrated into the consolidated Check Point Infinity Architecture that protects customers from sophisticated Gen V mega-cyber-attacks. It can be easily and rapidly deployed on existing Check Point Security Gateways and seamlessly integrates with multiple identity sources.
Specifications:
| Supported Appliance Families | |
|---|---|
|
|
| Supported Operating Systems | |
|
|
| Software Blades Interoperation | |
|
|
| Identity Agent Platform Support | |
|
1 IPSO supports identity enforcement and logging. For identity acquisition (AD Query, Captive Portal and Identity Agents), use a SecurePlatform gateway and share the identities with the IPSO gateways.
2 Identity Awareness support coming soon
Documentation:
Download the Check Point Identity Awareness Datasheet (PDF).

